
This week I was in the fortunate position to be able to attend a five day workshop at de Waag in Amsterdam. Julian Oliver and Danja Vasiliev hosted Behind The Scenes of the Internet.
The workshop opened with a presentation on the influence of engineering on society. Julian and Danja refer to themselves as critical engineers and have a clear understanding of the deep influence of technology on how we relate to each other (“Look at what Easyjet has done to the shape of Europe.”).
According to them we have more and more black boxes (often locked down) which place a rich interface (a marketing, business or political decision) between the person and the device while at the same time being very intimate to us: think about the iPod Nano in your pocket (and compare it to the old grammophone). Opening these blackboxes (essentially hacking) should then be considered research. The right to open the things we own, if only for study, is increasingly contested. This is problematic because they think technology you depend upon should be understood.
They define the Internet as a deeply misunderstood technology that we have become deeply dependent on. Somebody does own (parts of) the Internet. When they did a workshop in Peru they found out that all of the Internet traffic in that country was routed through Telefonica, giving Spain the hypothetical power to turn off Peru’s Internet when they want to. The question of geography is interesting on the Internet. Where are you on the Internet? Can you access your data and get to it? What will they say when you show up at a data center and request your files? Olver and Vasiliev consider the cloud to be a dangerous form of reductionism.
McLuhan writes in one of his introductions for Understanding Media:
The power of the arts to anticipate future social and technological developments, by a generation and more, has long been recognized. In this century Ezra Pound called the artist “the antennae of the race”. Art as radar acts as “an early alarm system,” as it were, enabling us to discover social and psychic targets in lots of time to prepare to cope with them. This concept of the arts as prophetic, contrasts with the popular idea of them as mere self-expression. [..] Art as a radar environment takes on the function of indispensable perceptual training rather than the role of a privileged diet for the elite.
Julian and Danja showed their abilities as a radar by talking about some of their artistic projects that they are working on to try and problematize these topics. Julian has just made something he calls the Transparency Grenade, a little computer wrapped in a grenade shaped holder which start snooping on the wireless netwerks around it whenever you pull out the pin. Danja is working on Netless which tries to be a network of nodes that connect to each other independently from the net. Both of them showed worked in a recent exhibit for which the Weise7 book was created. It is a box shaped like an old-fashioned book with a computer inside. When you open the book it becomes a Wifi access point that allows you to read all the information about the exhibit. When you close the book, the computer turns itself off. They also created a project that plays with what they call the “browser-defined reality”: NewsTweek which used the faux sloga: “Behind every mind is a network. Own it. Fixing the facts. One hotspot at a time”. I’ve written about this project before. It allows you to change news sites in your local wifi network. You can check what people are changning on the NewsTweek Twitter account.
All workshop participants then got a specially designed virtual machine full of networking tools that we could run in VirtualBox. Everybody had to get up to speed with the command line which got a wondeful ode by Julian: Knowing the command line is great because it is a shared language across many machines. You are talking to the computer and it is talking straight back to you. You ask and the computer responds. You can take the output of one program and make it the input of the next program. It allows you to automate the operating system (rather than the computer turning you into a proletarian clicking machine). The command line is far from going away. As computers get smaller, the command line interaction becomes a dominant model.
The artists gave us a crash course on how to use the command line interface. I love how they desribed moving between the directories as moving inside the spatial landscape of your computer. We quickly moved on to commands like netcat (or nc), ifconfig, arp arp-scan, ssh and scp. We discussed what a network packet consists of, the header (SRC, DEST, LEN, SWQ) and the body with its payload.
On the fourth day we got a short lecture on routing and how to set your default gateway on the command line. At that point in time we had created and configured our own little network and were able to ping eachother, log into each others machines and go online using the “base” computer as the gateway and our local DNS server.
In the afternoon we explored the inherent vulnerabilities in using open Wifi networks. By using Aircrack and Driftnet we were able to see images scrolling by from sites that people were browsing on a public Wifi network in a local bar. Driftnet’s manual says the following:
Driftnet watches network traffic, and picks out and displays JPEG and GIF images for display. It is an horrific invasion of privacy and shouldn’t be used by anyone anywhere.
This blog is very much my notebook too. I therefore want to make sure I keep the following three commands (in this order):
[code language=”bash”]
sudo ifconfig wlan0 down
sudo airmon-ng check kill
sudo airmon-ng start wlan0
sudo airodump-ng mon0
[/code]
The final day was about how to protect yourself a bit better online (a lot of the participants had started to feel “naked” after the Wifi snooping sessions of a day earlier. We discussed how encryption helps you with your basic human right to privacy while in the public space called the network and looked at the difference between anonimity and encryption. They explained HTTPS and Tor with this live diagram from the Electronic Frontier Foundation (EFF):
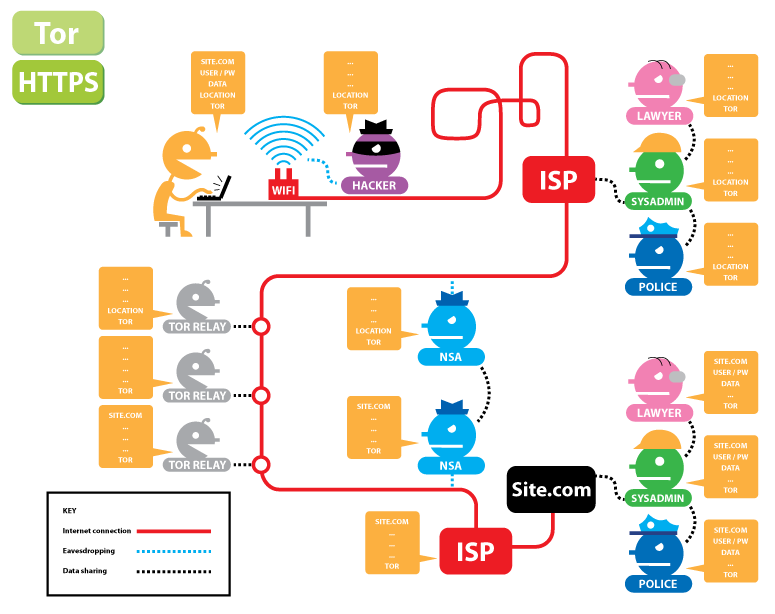
They also made us download the the Tor Browser Bundle and discussed a few handy Firefox addons:
- GoogleSharing to anonimize your Google searches.
- User Agent Switcher allows you to change your browser user agent so that the webpage thinks you are using a different device.
- HTTPS everywhere to force your browser to use HTTPS whenever it is available.
- DoNotTrackMe helps to protect you against companies tracking you online (they want to do sentiment-analysis and try to pre-empt your behaviour.
We looked at setting up a VPN which is great tool to protect you against Wifi sniffing and to quickly . They showed us ipredator and OpenVPN and have inspired me to finally turn on the VPN capabilities of my VPN server.
Finally they shared a link to their Cryptoparty Handbook. This 400 page book was written in four day sprint and provides a comprehensive overview of everything that we learned (and much more).
For many participants this workshop was a truly transforming experience, hopefully changing their relationship to technology forever. I need to thank Dorien Zandbergen for masterminding this and making it possible!